SELF-DEFENDING NETWORKS
Self-Defending network approach is used to reduce or minimize the attacks on the system, improve the reliability and moreover creates autonomous systems which act as a solution to respond, make a decision on security. It is something which could react to a threat. There are always some or other issues with the network security such as DNS problems, duplicate IP addresses, IP address exhaustion, slow internet performance, unable to connect to internet, sharing the data or transferring the data, unable to perform a call, email based spams, unauthorized activities, spy ware and many more.
Problem
Issues recently faced by me are slow internet, making or receiving a call using Vodafone network. As dated on 8th of June 2019 many people of Australia faced a network outage of Vodafone. Most of the reported issues are regarding network issues (53%) and mobile data (44%).

fig 1: Vodafone network outage map Australia.
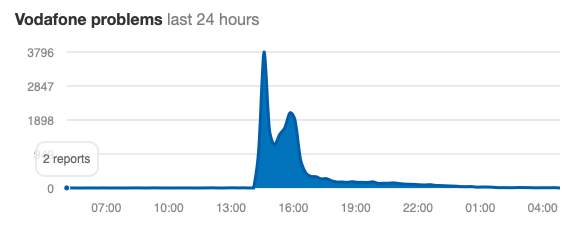
fig 1.1: Chart time vs number of reports.
The main challenge is to recognise the threat and the causes for it so that it can be resolved within no time. This is not a human intervention and requires this type of rapid response to resolve the issues. This can be due to the server issue or the connection issue.
Problem Identification
Basically, a network outage is an issue where there is no defect with the server but there is an issue with the internet connection between the system/mobile and the server. Server hardware failure may also be one of the major reasons for a network outage. It can also be caused because of routing issues which are outside our control. People also come up with issues such as a dialogue popping up which says “site is offline” even though your internet connection is of full strength and server running fine. People face this issue when the network outage is due to routing issues. The third-party monitoring service reports the site as offline for those who are affected by the routing issues.
Some probable causes of a network outage are: 1) Hardware failure.
2) Faults in network devices.
3) Routing issues.
4) DNS configuration.
5) IP addresses.
6) Hardware-Software incompatibility.
7) Network congestion.
8) Power interruption.
9) Security.
10) Human errors.
According to TechRadar, the 5 world’s biggest network outages are Dyn cyberattack (2016),
British airways IT failure (2017), Amazon Web Services (2017), Vodafone Data Centre (2011),
Whole Republic of America without connection (2011), adds up saying right IT systems in place can protect the organisation from being offline.
Wonder why it pops up “Failed to open” and “safari can’t open the page” even though you have full strength signal and server working fine, as mentioned above it’s because of the third-party monitoring service which reports it as offline for those who are affected by routing issues. This is the point where many of us are ambiguous, check for the connection turn on and off the internet, restart the system. These third-party services monitor the uptime, downtime and availability of the service, gives the detailed report of the performance data.

fig 2: failed to open page.
Ways to solve the issues which lead to network outage
1. IP Addresses
One cannot access the network if two same devices tries to share the same IP address. This is often due to router’s default DHCP configuration. This ambiguity is probably because the DHCP of new device tries to assign addresses beginning of the subnet while, the older device may already have static IPs occupying same lower number addresses.
Device 1: 192.168.1.2
Device 2: 192.168.1.3
This could solve the issue or else just turn off the DHCP server on the new device as it may have its own server.
2. Hardware failure
In a network there are n number of interconnected hardware elements so, there are more chances of network outage even if a single critical element fails. It can lead to a failure of any device, such as network controller, router, server etc… If this is the case, we need to quickly recover the element or to get new device online by automatically backed up device configurations.
3. DNS configuration
We can easily come to know that this is the issue, if we face errors such as name of DNS does not exist, network path not found. This can be resolved by checking the IPV4 TCP/IP settings of the adapter and select “obtain DNS server automatically”. Using incorrect DNS can also lead to slowdown of internet speeds because of routing congestion.
4. Router issues
Network monitoring software helps in identifying and gathering the data from all the network devices and their performance statistics which include uptime and downtime. This software can also detect what caused the device to go down, which device and where it is located.
5. Security
Network security is the critical subject to be taken into consideration. Because privacy plays a major role today. To make sure your device is secured, you need to keep a regular audit on the configuration infirmity. Need to protect it from unauthorized changes. Unauthorized access to be prohibited. Technically one can create a MOTD banner using he command line.
6. Connection issues
When a single workstation pops up with a message stating “No internet” while opening a browser then it’s obvious that the network is working fine but there may be some fault in the hardware or software of this particular system. We just need to make sure if all the connections are right, eliminate the communication barriers and make sure the ports are open to external network by checking the firewall software on the device.
The above mentioned are some of the causes of network outage and quick ways to resolve the issues or threats. Each issue also has a preventive measure to make sure they don’t pop up in mere future.
ENDPOINT SECURITY
Network security plays a key role to protect the information, devices against unauthorized intrusion in this corporate world. It also compliments endpoint security, which is now a days developing, as organizations bring together control of PCs, servers on their networks to protect it from unauthorized access. It is the form of computer protection.
Self-Defending Network (SDN) concept is founded to offer endpoint protection to the devices, application security, intelligent response etc… All the above-mentioned ways to keep the network secure uses proactive defence mechanisms whereas SDN uses adaptive defence mechanisms so that it makes sure its active every time, reduce the threats, quickly respond and perform the task in an easy way. Cisco based self-defending network gives access to the customers to use the infrastructure with less threats and security.
Cisco SDN also continues to improve quickly responding to a threat.
First phase of security includes elements such as switches and routers (Integrated security).
Second phase involves improving links between security elements such as switch, routers and extending the presence of network onto endpoint which connect to a network (Collaborative security).
Latest phase consists of Adaptive Threat Defense (ATD) which has the capability to react to the threats from Anti-X technologies.
As mentioned SDN quickly reacts to a threat whereas all the above-mentioned ways to reduce risks create or control a situation rather than reacting to it. SDN deals with the threat rather than controlling or creating. Instead of traditional ways of approach which follows defense-in-depth i.e., figuring it out where the issue is, where it is located, and then controlling it, SDN is moreover an automated way to quickly respond to a threat and act as a backup plan. It has the details of the threat event information, implication of it occurring, actions to take, appropriate systems to make sure actions take place in real-time.
What if there is a new threat?
Cisco SDN has the ability to identify non-compliant networks threats when they occur, react with appropriate measures and minimizes the effect. The above-mentioned are the services which provide the ability to exchange which makes sure these services assist SDN in reacting to changes in the network and quickly countering to the threats at the same time while they are occurring. Some threats such as E-mail based spams, spyware and unauthorized end-to-end activities are some examples which are not effectively addressed by traditional ways of approach (firewall, Network IDS products).
Conclusion
CSDN is a security solution which includes every level of network security rather that limiting to specific layers and it has the ability to communicate and share the valuable information among various security devices. This is a must and important evolution in the terms of network security.
References
1. https://help.crucial.com.au/hc/en-gb/articles/203293600-What-is-a-network-outage-
2. https://downdetector.com.au/status/vodafone
3. http://www.ciscopress.com/articles/article.asp?p=379750
4.https://www.cbtnuggets.com/blog/2018/12/7-common-network-issues-and-how-to-resolve-them-fast/
5. https://www.cbtnuggets.com/blog/2018/06/what-makes-networking-difficult/
Cite This Work
To export a reference to this article please select a referencing style below:


