Man in the Middle and Man in the Browser Attacks on Financial Institutions.
Abstract
Four decades ago, what started as a US military research initiative to build network for linking US universities and research centers is now the Internet. Today it has expanded to every corner of the globe (Privgcca, 2016). The number of Internet users has risen from few computer scientists to 3.17 billion users. It has helped in reducing costs of communication as one can easily be in touch and communicate with each other with the help of chatting, email applications and online transactions/payments (Friedman, 2014). It has also helped organizations to offer better customer service, reduce amount of paper work, increase productivity, and enable customers to perform enquiry and transactions anytime and from anywhere. This paper will be focusing on the importance of online banking/transaction security.
Introduction
Banking organizations have been developing for years in a broad scope and have started to replace more traditional banking techniques in certain fields such as processing cheques, making transactions and money transfers to online, therefore; payment systems are constantly undergoing radical changes. More security measures are present but the users of these systems must also be allowed decent compatibility. Due to the amount of modern day threats these banks have also been facing a vast amount of risk and vulnerability exploitations, banks are usually very concerned about two kind of attacks, man in the middle attack (MITM) and man in the browser attack (MITB). As a result, financial institutions must ensure to provide effective authentication techniques. These two attacks (MITM and MITB) will be the main concentration and the focus of the analysis will on these attacks as well.
The Two Common Attacks.
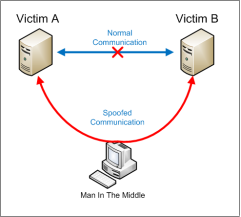
The Man in The Middle and Man the Browser are the very predominant attacks in the finance industry. The difficult part is identifying each type of attack and taking precautionary measures from either attack. MITM occurs when a hacker can see and modify the communication between the client and the bank, it makes both parties believe they are directly communicating with each other to deceive but there is usually an attacker eavesdropping. Therefore, this is very common on unsecured and unprotected networks. On the other hand, MITB uses malware to infect a web browser. This is done by the malware exploiting vulnerabilities in the browser security which enables them to modify and manipulate the page.
Getting Technical, MITB vs. MITM
One of the few important differences between these two attacks is that MITM attacks operate at the network layer whereas MITB operate on the application there, in this case on the web browser. Although MITM attacks remain popular attackers prefer MITB as banks may use sessions ID’s to identify MITM attacks. Using session ID’s banks can determine whether there has been malicious activity during a transaction and notice the fraudulent attempt and consequently cancel it. By giving the customer’s device a unique ID, the bank can then use algorithms to analyze and link the multiple user sessions from where they typically perform their banking (Eisen, 2012). MITB attacks are a lot more deceitful, they completely take control over the user’s website and control the browser while the user thinks everything is normal. The attackers in this scenario alter web views and account balance without the users knowledge. Once the user logs in they can also redirect any sensitive traffic to an attacker’s system, while keeping the original SSL/TLS protections intact (Trusteer, 2013).
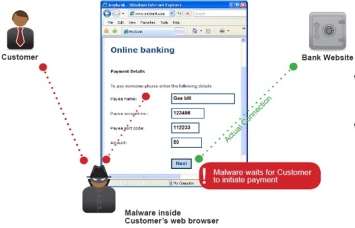


MITB
People are very commonly exposed to the risk of these attacks due to the browser security problems in the case of MITB browser extensions are frequently the malware which allows the attacker to exploit the vulnerability. Browser extensions are frequently portrayed as useful software which enhance user experience but is malicious software or code. This is known as a Trojan. Browser extensions may be plugins, Browser Helper Objects (BHO), JavaScript and add-on features.
Get Help With Your Essay
If you need assistance with writing your essay, our professional essay writing service is here to help!
The functionality of BHOs is usually to provide add functionality to a browser these could be written by the attacker with programming experience. The problem with BHOs is that they can hide from antivrus this makes them undetectable. In a MITMB attack these are used to change a site, add fields, remove fields. They also can add registries to the system and load at booting (Utakrit, 2009).
Grease Monkey is a popular add on for chrome which can allow a user to change the appearance of a website or eliminate ads. This JavaScript is not malicious but it uses the same methodology as the malicious JavaScript applets. The danger of add-ons is that they can easily monitor and retrieve the users’ information at any time.
SSL has been thought of as a solution by some security experts for MITB attacks but even this control has been proven to be ineffective. The reason for this is that the attacker injects or gives the user a Trojan which carries out malicious activities directly inside the browser. Therefore, no suspicious activity is detected.
MITM
MITM are less common as security professionals have learned ways to mitigate the attacks that use this method. It is also widely known as session hijacking. In this case, the attacker usually seeks vulnerable hotspots or networks. The attacker would usually direct the victim to a fake login page of a website (perhaps a phished paged) and then get the credentials as soon as they are authenticated. The attacker could then simply access the account and withdraw money or make transactions. Security measures such as the OTP are not effective as defense against this attack as the attacker could fraudulently capture the temporary password and forward it on the portal in the 30 – 60 seconds provided. In this attack the main issue is that the user has no way of being sure or verifying who is asking for information. As a result, two step verification is also considered vulnerable.
Protective measures.
The security triad which is an important principle to security experts evolves around three elements. C- Confidentiality, this means do not allow unauthorized individuals to access or see data or systems. A- Availability, which means ensure the system/data is available when needed. I- Integrity, if data or a system or in this case a transaction it loses its’ integrity which means it has been manipulated with. In the case of transactions, Integrity is a very important principle. Banks and financial institutions need to always ensure the integrity is maintained. By doing so, we need to implement controls, also known as countermeasures.
User Protection Strategies and Controls
MITB
In order to minimize these attacks the knowledge has to be known on either side of the equation, the users should be aware as well as the bank. Users can take precaution by installing anti virus, although not entirely effective it does depend on the detection capability and reduces the chances. Secondly, use a hardened browser in a USB drive, this will provide moderate protection. Thirdly, only do online banking with banks who are aware of these kinds of threats and implement countermeasure. Ultimately there is risk in every procedure, unless you are will to completely not use online banking there will always be risks and threats.
MITM
??
Mitigation for Banks.
MITB
As previously mentioned, attackers have also learned how to compromise two step authentication as well the same also applies to captcha and others. The malware can simply wait till the user has authenticated himself. It can also intercept and modify response when using SSL or encryption. Moderate protection could be offered by the bank itself providing clients with Hardened Browsers on USBs containing cryptographic smart tokens for authentication. The hardened browsers are harder to infect. Similarly, OTP token with signature would be effective, the user would have to re-enter the transaction details to the OTP device and then it could generate a signature based on that in that way it would not match if the MITB alters the request, this is also rather inconvenient. Fraud detection based on transaction type and amount is also sometimes effective, in the case of an abnormal transactions some banks call the client to check if it is genuine or not. User profiling could also be used.
MITM
??
Cite This Work
To export a reference to this article please select a referencing style below:


