Tor Battlefield: Infiltrating Darkweb Operations
Technology utilized by law enforcement to investigate and respond to criminal activity and terrorism has rapidly evolved to increase efficiencies in identifying and pursuing suspects in both the real world and the Internet. One challenge with identifying suspected criminal parties on the Internet lies with the use of Anonymous Communication Networks (ACN) to hide client-side TCP activity. “The Onion Router”, known as Tor, is a popular free software that offers anonymizing browsing services. An established Tor session allows users to navigate through web content that is nearly invisible to the public eye, known as hidden services, while minimally exposing personally identifiable information. These hidden services are given ‘$16characterhash.onion’ addresses and are common catalysts for hosting criminal content such as child pornography, contract hackers and killers, counterfeit government documentation, drug marketplaces, and many other various forms of universal contraband. Many repositories for illegal or malicious content hosted on Tor’s hidden services remain easily accessible while the responsible hosting parties remain anonymous. In recent times, large-scale federally led operations were successful in leading to the shutdown of multiple major illegal operations around the world which were hosted on the Tor network and arresting the responsible parties. Two of the major illegal marketplaces that were busted were known as Silk Road, a drug marketplace; and Playpen, which hosted child pornography. A common theme among the successful operations against anonymous criminal organizations involved infiltration of the operations by undercover officers using the Tor service. Identifiable information of customers and hosting parties were obtained by law enforcement through a combination of zero-day software exploitation, social-engineering techniques and thorough network analysis. Another notable method used to capture criminals using Tor’s hidden service assets as a medium to conduct malicious activities is the tactical use of honeypots. Honeypots are monitored, vulnerable assets hosted by surveilling parties which objectively attract a targeted audience to engage in activity, resulting in the potential exposure of criminal parties. This research paper will discuss the effectiveness of various information collection and network analysis techniques along with infiltration methodologies used to expose illegal activities hosted on the Tor network.
Literature Review
To examine techniques of collecting information and performing network analyses on web activity using Tor, the mechanics of Tor need to be defined properly. Tor offers a browser on their website (https://www.torproject.org/projects/torbrowser.html) This bundled software package includes a browser that is preconfigured to minimize all personally identifiable network activity after installed on the client. Once a session is created, Tor bounces all outgoing communications between three or more volunteer hosted nodes through a tunneling process that can automatically or manually select a path between client and server. Each communication between nodes is negotiated and authenticated via public-key authentication. Figure 1 shows an example of an SSH-handshake using the Tor services, communication in the middle grey area is where all traffic is practically invisible to outside parties as the traffic is encrypted between each route and again when returning to the client (Cao & Huang, 2018).
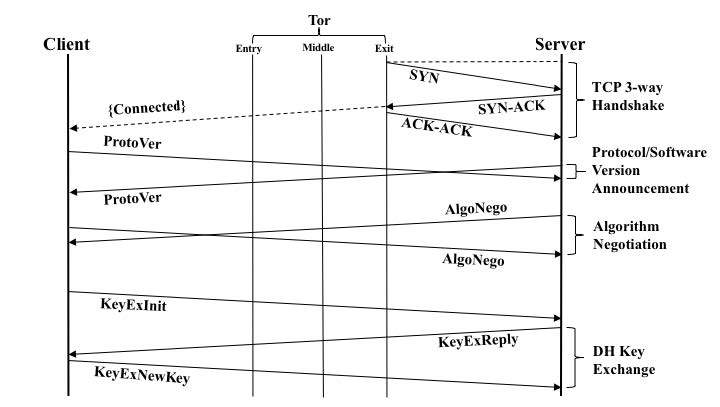
Figure 1: SSH Handshake through Tor (Cao & Huang, 2018, p. 476)
With the basic framework of Tor defined, the next step of this research is to identify the vulnerabilities of Tor as a medium to conduct criminal activities. How can law enforcement positively identify malicious web activity originating from Tor exit nodes? The most vulnerable area of this process is the communications between the client and the exit node returning data, especially if data is not using end-to-end encryption (Minárik & Osula, 2016). This information reveals that if government entities can compromise, engage in active surveillance, or even host Tor exit nodes to perform traffic collection and analysis leading to positive identification of illegal network activities. As stated by the onion specification documents, “institutions that want to monitor the activity of those connecting to the proxy, compromising an onion proxy compromises all future connections through it” (Syverson, Dingledine & Mathewson, 2004).
Get Help With Your Essay
If you need assistance with writing your essay, our professional essay writing service is here to help!
One such instance of legal exit node occupancy was during “Operation Pacifier”, an FBI operation to take down the child pornographic host site ‘Playpen’ accused of hosting 95 percent of the child pornography on the Tor network with sites attracting thousands of daily users (Eggestein & Knapp, 2014). The FBI took control of the servers hosting Playpen owned by a company called Freedom Hosting, to inject malicious scripts into webpages that would send back machine information of the visitors including their public IP address, which led to arrests of the hosts and many visitors of the site (Henri, 2017).
Since compromising Tor exit nodes, also known as creating ‘poisoned’ nodes, are required for accurate network analysis to identify illegal activities by criminal parties on the Tor network, what information can surveyors of the compromised node conclude? One specific instance involved research by performing a replay-attack in a controlled environment through two compromised nodes, the entry node and the exit node. The conclusion of the replay-attack revealed that “it can be used to randomly profile both clients and servers hidden by Tor. For any client who uses a circuit across the entry router and exit router, the attacker can discover their Internet behavior and compromise their privacy” (Pries, Yu, Fu & Zhao, 2008). Like the replay-attack previously discussed, another method of attack against the privacy of Tor users is known as a Sybil attack, or when an attacking party client floods the network with poisoned Tor relays (Biryukov, Pustogarov & Weinmann, 2013). This attack can alter the onion routing algorithm by increasing the chance Tor users select a poisoned node route rather than benign nodes(Bauer, McCoy, Grunwald, Kohno & Sticker, 2007). The Tor routing algorithm can discriminate exit-nodes based on multiple varying attributes, such as hosting service and navigation target (Singh et al., 2017).Since users of Tor can volunteer themselves as an exit-node relay, the traffic passing through the ‘poisoned’ exit node to the clients can be compromised under poor encryption (Bauer et al., 2007). If the compromised payload returning to the client from the exit node concludes that analyzed traffic stems from a hidden service flagged for malicious services, the receiving party may be identified from the compromised payload, and appropriate legal action can take course. This transitions to observed method of Tor activity observation through the setup of honeypots, particularly as Tor hosted hidden services (D1.1, 2006).If law enforcement agencies can propose hosting many monitored Tor exit nodes and honeypot hidden services, the previously discussed attack vectors could collect intelligence against Tor users seeking and hosting illegal content, increasing the overall deterrence to use Tor for illegal activities.
Discussion
Through analyzing major successful operations using anonymous networks like Tor, all criminal parties of the recent cases including Operation Pacifier, Operation Onymous, and Operation Bayonet had been compromised through infiltration of their activities via exploitation of Tor’s architecture, careful social engineering practices, open-source intelligence gathering or negligent operation. Not all methods discussed in this research paper will lead to the end of all digital crime, but as a great stepping stone towards providing justice to those hosting malicious content available to the public. Some limiting factors of these methods discussed include the abundance of controlled network environments, known vulnerable configuration controls and lack of surveillance infrastructure regarding infected exit nodes.
Find Out How UKEssays.com Can Help You!
Our academic experts are ready and waiting to assist with any writing project you may have. From simple essay plans, through to full dissertations, you can guarantee we have a service perfectly matched to your needs.
View our academic writing services
Tor has been proven to be a vulnerable program, however many additional mediums can be set in place to increase the likelihood of users remaining anonymous against attack vectors discussed in this paper. The resulting operations also proved to decrease illicit market activities on Tor’s hidden services (see Figure 2).As stated from a journal on ‘Computer Law & Security’, “Little information on how [law enforcement] managed to ‘break Tor’ has been leaked, other than that the methods are not revealed because they are ‘sensitive’…” (Minárik & Osula, 2016), meaning exploitation must still exist given the global resources given to the investigating parties world-wide. Web-crawling algorithms have been developed and tested to unveil hidden services, however to find new occurrences of malicious hidden services, the required number of poisoned entry nodes increases (Nepal, Dahal & Shin, 2015).
There exist many legal boundaries to consider when actively collecting user data, outlined in international documents such as the Council of Europe’s ‘Declaration on freedom of communication on the Internet, the United Nation’s ‘Report of the Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression’, and the United Nation’s ‘Report on encryption, anonymity and the that protect user privacy and the human rights framework’ (Minárik & Osula, 2016). For example, the Council of Europe requires authorization to conduct surveillance, or evidence collected against parties may be dismissible in court (Minárik & Osula, 2016).
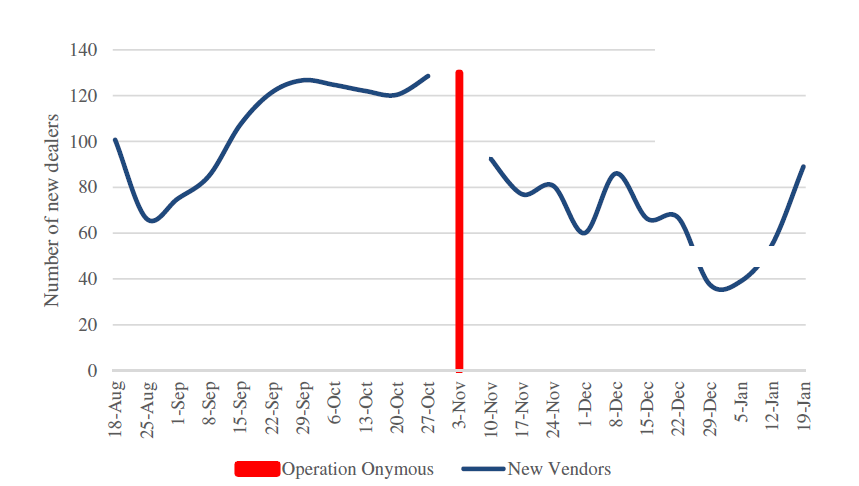
Figure 2: Dealer Account Activity After Operation Onymous (Décary-Hétu & Giomanni, 2017)
Opinions and Conclusion
While laws may be in place to protect the privacy of online activity in both the ‘Clearnet’ or through anonymizing services like Tor to access the ‘darkweb’, strategic surveillance efforts must be put in place to unmask those partaking illegal activities on the internet. Cooperation of investigating parties is required to continue the ongoing research to crack tunneled network traffic to promote cybersecurity. Law enforcement must continue to utilize infiltration tactics via exploits, social engineering and hosting monitored Tor exit nodes to gain intelligence on these criminal enterprises to ultimately compromise and eliminate dangerous content from the public hand. Baiting malicious activity using honeypot systems has great potential in identifying illegal parties utilizing Tor services in combination with the attack vectors used to identify parties. Only time will reveal additional research and methodologies to unmask criminals and terrorists using Tor as an instrument of anonymity.
References
- Bauer, K., McCoy, D., Grunwald, D., Kohno, T., & Sicker, D. (2007, October). Low-resource routing attacks against tor. In Proceedings of the 2007 ACM workshop on Privacy in electronic society (pp. 11-20). ACM.
-
Biryukov, A., Pustogarov, I., & Weinmann, R. P. (2013, May). Trawling for tor hidden services: Detection, measurement, deanonymization. In Security and Privacy (SP), 2013
IEEE Symposium on (pp. 80-94). IEEE. - Cao, Z., & Huang, S. H. S. (2018, August). Detecting Intruders and Preventing Hackers from Evasion by Tor Circuit Selection. In 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE) (pp. 475-480). IEEE.s
- Décary-Hétu, D., & Giommoni, L. (2017). Do police crackdowns disrupt drug cryptomarkets? A longitudinal analysis of the effects of Operation Onymous. Crime, Law and Social Change, 67(1), 55-75.
- Eggestein, J. V., & Knapp, K. J. (2014). Fighting Child Pornography: A Review of Legal and Technological Developments. Journal of Digital Forensics, Security and Law, 9(4), 3.
- Greece, F. P. C., Germany, D. C. P. C., Greece, V. P. C., & France, A. P. C. D1. 1: Honeypot Node Architecture.
- Henri, V. (2017). The Dark Web: Some Thoughts for an Educated Debate. Canadian Journal of Law and Technology, 15(1).
- Minárik, T., & Osula, A. M. (2016). Tor does not stink: Use and abuse of the Tor anonymity network from the perspective of law. Computer Law & Security Review, 32(1), 111-127.
- Nepal, S., Dahal, S., & Shin, S. (2015, January). Deanonymizing schemes of hidden services in tor network: A survey. In Information Networking (ICOIN), 2015 International Conference on (pp. 468-473). IEEE.
- Pries, R., Yu, W., Fu, X., & Zhao, W. (2008, May). A new replay attack against anonymous communication networks. In Communications, 2008. ICC’08. IEEE International Conference on (pp. 1578-1582). IEEE.
- Singh, R., Nithyanand, R., Afroz, S., Pearce, P., Tschantz, M. C., Gill, P., & Paxson, V. (2017, August). Characterizing the nature and dynamics of Tor exit blocking. In 26th USENIX Security Symposium (USENIX Security). USENIX Association, Vancouver, BC (pp. 325-341).
- Syverson, P., Dingledine, R., & Mathewson, N. (2004). Tor: The secondgeneration onion router. In Usenix Security.
Cite This Work
To export a reference to this article please select a referencing style below:


