CHAPTER -VI
6. CONCLUSION & SCOPE OF FUTURE WORK
There are some key aspects to discuss about this thesis in general. First, it is important to mention that the main objective of this work – implementation of a palmprint recognition system – was successfully accomplished. Biometrics plays an important role in personal identification. The importance of biometrics in everyday life has been discussed and different biometric technologies are introduced. It has been shown that palm can also be a good biometric. The work reported in this thesis is summarized in this chapter. This Research Work proposed a novel approach for Palmprint Biometric Authentication System to identify the individuals based on their palmprints. The approach novelty could be found in the combinations between palmprints images transform techniques, features reduction technique and feed-forward neural network classifier. CASIA pre-processed hyperspectral database and MATLAB version 2016a with supporting toolboxes were used in our experiment work. Firstly, each pre-processed palmprint image has read by MATLAB internal function, and it has transformed by using multiscale toolboxes in order to convert each image into data. The resulted data is projected by dimensionality reduction tool. Finally, neural network toolbox used for recognition training and verification the resulted vectors. We manually prepare proposed Gabor Wavelet and Local Binary Pattern function along with all Other function in MATLAB 2016 and a database of 200 palm images of 20 people is considered for the validation.
Get Help With Your Essay
If you need assistance with writing your essay, our professional essay writing service is here to help!
This Thesis Work considers a novel and efficient method for the palmprint identification based on Gabor wavelet by using multi-block local binary patterns. Proposed method is further supervised through our proposed multi-layer feed-forward neural network for more accurate and computationally efficient recognition. Gabor wavelets efficiently filter the pre-processed image for getting optimum texture features through MB-LBP. Due to accurate feature representation of palm images through proposed LBP, anticipated MLFFNN training rate is high and we are getting much accurate results comparatively.
Experiments are performed to make an analysis for the optimal palm region and LBP neighbourhood. We investigate the matching accuracy for the optimal parameters. The performance of the proposed method in term of accuracy and some other parameters is obtained and compared with some recent methods. These local characteristics are summed and orientation corresponding maximum local intensity pattern is conceded as optimal local direction. Micro pattern representation is obtained by LBP descriptor. Feature vector is prepared by histograms of 256 bins. In our proposed scheme we use the Gabor wavelets, which has wavelet like property, in orthogonal direction and smoothest contours. Orientation extraction is done optimally to get directional representation and feature size is reduced by extracting LBP histograms. Accuracy of Proposed system is about 99.6% and error rate is below 0.9%.
Compared to other existing method proposed method provides robustness to noise, low complexity and small features length. Secondly 3x 3 direction pattern employed which extract the edge characteristics locally. Direction pattern further emphasis edge orientation and filter out non edges along irrespective direction of pattern. Local aggregation gives higher 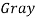 value (Local Intensity) at particular orientation. So, the competition for maximum local intensity can better select the orientation information. Secondly orientation information is not affected by intensity variations. Because of these reasons, it is obvious that our method is performing well. In this palm print recognition system, features such as region mask, orientation field and minutiae are being extracted. An efficient matching algorithm is being implemented which uses these features for comparison of the query palm print with the database. Hence this system tests the image with the database and checks if the person is authenticated or not. This authentication system can be used in forensic science and other border control systems for authentication of palm prints. the proposed work is also tested on colour RGB (multi-dimensional) images and real time palm images.
value (Local Intensity) at particular orientation. So, the competition for maximum local intensity can better select the orientation information. Secondly orientation information is not affected by intensity variations. Because of these reasons, it is obvious that our method is performing well. In this palm print recognition system, features such as region mask, orientation field and minutiae are being extracted. An efficient matching algorithm is being implemented which uses these features for comparison of the query palm print with the database. Hence this system tests the image with the database and checks if the person is authenticated or not. This authentication system can be used in forensic science and other border control systems for authentication of palm prints. the proposed work is also tested on colour RGB (multi-dimensional) images and real time palm images.
Further Works
For future work, the combinations between another multiscale image transformation such as 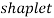 ,
, 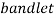 ,
, 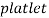 and other will be taken in addition to use alternative features reduction methods such as ICA, kernel PCA and other contemporary techniques are suggested to be used. In addition, the classifier type is suggested to change to show how the recognition accuracy could be improved.
and other will be taken in addition to use alternative features reduction methods such as ICA, kernel PCA and other contemporary techniques are suggested to be used. In addition, the classifier type is suggested to change to show how the recognition accuracy could be improved.
Although cancellable biometrics overcome the weakness of cryptography, current cancellable biometrics are still not secure enough for the palmprint identification. For example, attackers can still insert stolen templates replay and database attacks before systems can cancel the stolen templates and reissue new templates. Furthermore, current cancellable biometrics cannot detect replay and database attacks. In other words, if attackers insert unregistered templates into data links or databases, systems cannot discover the unregistered templates. To solve these problems, we can take advantages of cryptography and cancellable biometrics to design a set of security measures to prevent replay, brute force and database attacks for secure palmprint identification.
One could improve the registration accuracy and the image combination process. A detailed study needs to be done on the effect of adding more frames for combination. This method could also be combined with the pose correction approach developed in the previous algorithm to make a robust system with further improved accuracy.
In addition to these further directions, biometric researchers are in fact facing some open problems. Most biometric systems are examined only on zero effort attacks (general false acceptance rates). Do they still survive if experts attack them? Furthermore, how can we objectively evaluate and compare the security levels of biometric systems? It should be recognized that successfully breaking into biometric systems depends on money, time and knowledge. Biometric researchers are facing a dilemma. As we write everything to disclose our findings and algorithms for the sake of distributing knowledge to our society and the next generation, we are also providing the information that potential attackers require breaking into our systems.
 Â Â Â Â Â Â Â Â
        
- Â (b)
Fig. 6.1 (a) A fake palmprint and (b) the corresponding genuine palmprint.
Cite This Work
To export a reference to this article please select a referencing style below:


