Infrastructure and security
Abstract
The evolution of the internet and networking has led to a dramatic increase regarding threats to information. Information is an asset and should, therefore, should be protected at all cost. The primary objective of TechLand’s network security is to protect the data. Network security ensures that digital information assets are preserved to maintain integrity, protect confidentiality and assure the availability of information when needed. The security of the router forms a vital part of the overall network security they serve. An attack or an error on the router can damage the security of the entire network. To ensure that the networks remain secure, it is essential for TechLand to monitor for attacks continuously as well as regularly test the state of its security infrastructures. The best network security strategies include establishing an effective security policy, staying updated with the latest hacking strategies and security communities, maintaining and monitoring the whole network system with sound administration practices.
Infrastructure and security
Introduction
Security on the local area networks (LANs) and the internet has been placed at the forefront of issues related to computer networks. The evolution of the internet and networking has led to a dramatic increase in the threats to information. Most of these threats cleverly exercise attacks that cause severe damage to many business enterprises. As the internet continues to grow, critical business applications become more prevalent on the internet with a lot of benefits. However, if the network is poorly secured, these applications and network-based services can pose a security threat both to an individual and the information resources of businesses as well as governments. TechLand Business Company believes that information is an asset and should, therefore, must be protected at all cost. We have to install effective network security to ensure that its digital information assets are protected to maintain integrity, protect confidentiality and assure the availability of information (Patel, 2015). Therefore, it is imperative that networks are protected from vulnerabilities and threats to ensure that business and companies attain their fullest potential. Careful management and auditing of the security features of TechLand’s system can ensure that the network has minimal downtime, improved security, and a decrease in network threats.
Network Protection and security
The primary objective of TechLand’s network security system is to protect its assets. Currently, networks regarding the modern world are more open especially with the initiation of the internet, personal computers, and LANs. As e-business and Internet applications continuously grow, it is critical that the company find the balance between being isolated and being open. With the increased security risks, it is vital for TechLand to enhance its network security features to enforce an access control policy between networks. Network protection has given businesses a balance between outbound access to the internet, commonly used for web surfing and email, and security. Security network refers to software and hardware features, functions, accountability measures, operational procedures, access controls, management and administrative policies required for the basic acceptable level of protection for software, hardware, and information within a given network. The security of a network is the most crucial part of the business information. The security network responsible for secure information passing through a networked computer (Patel, 2015). For successful prevention of loss of data, the proposed network security infrastructure will have to follow three fundamental precepts.
Get Help With Your Essay
If you need assistance with writing your essay, our professional essay writing service is here to help!
First, TechLand’s secure network infrastructures will have to consider the integrity of the information. It is the responsibility of TechLand ’s network infrastructures to ensure that all the information stored in the network will always be correct and protected from willful alterations and fortuitous data corruption. Second, the company’s network infrastructures will have to ensure the confidentiality of the information. The system of the company will have to allow sharing of information with only the intended parties in the network. Lastly, the company’s network system will have to ensure the availability of data. The authorized users within the network must be able to access their information at any time without exceptions. The real world network security entails detections, response, and prevention (Hansen, 1997). If the mechanisms of prevention are perfect, there is no need for detection and response.
In most cases, prevention mechanisms are perfect. However, without the detection and response mechanisms, the prevention has limited value. Detection and response are cost-effective as well as more effective than relying on more prevention. There are many preventive mechanisms in a network protection to secure networks properly against threats.
These mechanisms include addressing the actual physical layout of the network to ensure that it is adequately equipped, incorporating firewalls and encryption in the network to heighten the security and using several passwords with variations of characters to increase its strength. The appropriate authentication process is a fundamental part of the administrative step in safeguarding a network. A firewall is used to improve the network security level. It is a portal where authentic information passes through. One side of the firewall has information from the outside with possible undesirable threats of other networks and on the other side is the internal business network that should remain secure. There are three major types of firewalls. These types include application-level gateways, packet-filtering gateways, and circuit-level gateways. A packet filtering router is designed to enable the network to determine the secure connections that can be allowed to pass through the router to the LAN and the insecure connections that will be denied.
The application-level gateway authenticates the user for individual applications and its primary function of the firewall for identification and validation is the user. It then provides the user access to specific applications such as file browsers or E-Mail depending on the user requests. The circuit-level gateway has all the packet-filtering router functionality and does a bit more. The main enhancement is the use of identification and authentication of a user before accessing the in-house network.
Security Design Architecture
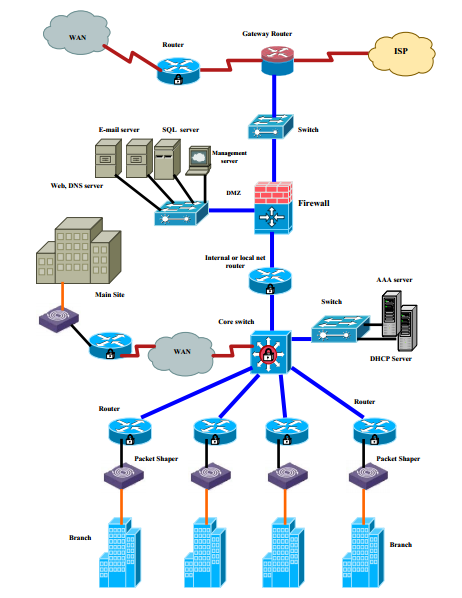
The figure projected security design of TechLand’s network infrastructure
The security architecture is usually incorporated into the existing network of the enterprise. The security requirements of each of the application service will be defined before the design of the security network. The security network will be divided into modules with an identifiable level of trust. Each security module will be treated separately and assigned a different security model. The goal of this approach is to have security layers so that the access of an intruder is constrained to a limited part of the network. Furthermore, the security architecture should define the type of security services that will be implemented across the network (Patel, 2015). These services include:
• Password authentication, authorization, and accounting (AAA)
• Security monitoring by intrusion detection systems (IDSs)
• Access (trust model)
- Confidentiality enabled by virtual private networks (VPNs)
Security Technologies
In this design topology, routers and firewalls configurations will be the main security guards of the proposed network. A router will be an essential part of TechLand’s network security. It controls the flow of data packets in a network and determines the optimal path for the data to reach its destination. The security of the router will form a vital part of the overall network security it will serve. An attack or an error on the router can damage the security of the entire network. The network will be able to address the following:
Identity
Identification is the accurate confirmation of the authorized users in the network, applications, hosts, resources, and services. The mechanisms of identity are important because it will ensure that access to the company’s network resources is only granted to authorized users while access by unauthorized users is denied.
Security of the Perimeter
The Security of the Perimeter controls access to critical network applications, services, and data is provided to legitimate users only. The routers and switches with access control lists (ACLs) will impose restrictions on the traffic it controls, therefore, ensuring that the perimeter of the enterprise network is secure. The firewalls will protect the network by examining all the data packets from the external networks attempting to access the network. It will reject the data packets that will not meet the required security restrictions (Patel, 2015). The security layer will provide secure communication between the source and the destination in an internet connection. The user and host processes will use application layer protocols to connect to the firewalls, routers and other devices within the network.
Secure Connectivity
TechLand must ensure confidential information by implementing various measures to protect the network against intrusion. Implementation of Virtual Private Networks (VPNs) ensures that the enterprise can have private, secure communications across its network. The router controls unauthorized and illegal intrusion into a network since it is used to connect two or more networks. Other security features of the router include IPsec and access control for secure networking.
Find Out How UKEssays.com Can Help You!
Our academic experts are ready and waiting to assist with any writing project you may have. From simple essay plans, through to full dissertations, you can guarantee we have a service perfectly matched to your needs.
View our academic writing services
The routers will be used to forward data traffic to the local networks within the enterprise routes. The interior routers will impose restrictions on the data traffic. The backbone routers will direct the traffic between the networks that make up the internet. The backbone router usually has a very low level of trust between the connected networks. The backbone routers will be configured to forward the data traffic without imposing restrictions as quickly as possible. The primary objective of this router is to ensure that authorized parties only do the operations and management of the router. The backbone router also ensures that the integrity of the routing information is protected. They usually employ exterior gateway protocols to manage routes. The border router is used to forward traffic between the external networks and the business enterprise. The main feature of the border router is that it forms a boundary between the untrusted external networks such as the internet and the trusted internal networks. A border router will employ routing protocols to impose those restrictions or use static routes. Furthermore, the router will provide multiple management configuration interfaces, remote maintenance and monitoring of the network (Patel, 2015). These features affect the confidentiality, integrity, and availability of the data connections, therefore making the router a crucial security component of the network.
Security Monitoring
To ensure that the networks remain secure, it is essential that TechLand continuously monitor for attacks as well as regularly tests the state of its’ security infrastructures. The filtering functionality of the routers enables them to protect the computer and other components of the network. Other features of a router include relaying functions, encryption and monitoring data streams
In a computer network, there are types of vulnerabilities and threats that a device or a network may encounter. These weaknesses include
- Technological Weaknesses: these are the network and Computer intrinsic security weaknesses. They include TCP/IP protocol, network equipment, and operating system weaknesses.
- Configuration Weaknesses: these are weaknesses due to the setting and configuration of the security devices such as routers.
- Security Policy Weaknesses: these weaknesses are related to people who are eager to take on the security weakness. Security policy weaknesses sometimes create security threats that are unforeseen.
There are two main types of security threats, external and internal, to a computer network. Internal threats are usually stemmed by unethical or disgruntled employees. External threats, on the other hand, are generally caused by hackers. The hackers can use email attacks, IP snooping or password sniffers to obtain or view sensitive information in a network. Password sniffers work by executing a packet sniffer which monitors the network traffic passing through a machine on which the sniffer resides (Schneider, 2012). The sniffer can record passwords and usernames. IP spoofing entails obtaining the address name of a workstation from an information packet that has trust with another workstation. The hacker acts like one of the workstations and uses the relationship to gain entry into other work stations. Emails are incredibly vulnerable to different attacks (Patel, 2015). The hackers can then use these emails to gains access to a network which can jeopardize the security of the systems.
Security Policy implementation
In order to successfully protect the network against the mentioned types of threats attacks and other vulnerabilities, it is necessary that TechLand configures its’ routers and firewalls to achieve the best security infrastructure. A security policy is a formal statement, regarding the rules and regulations to be followed by employees who will have access to any corporate resource. The security policy of TechLand will determine the person authorized to install, move or uninstall the router as well as the firewall. The plan will also define the authorized person to change the physical configuration or connections to the firewall or the router. It will also determine the authorized Designates to log in directly to the router via the console or any other direct access connections of a port as well as define the password policy for user passwords and privilege or administrative passwords. The following configurations will ensure that the network will have the best security solutions.
- Ensure that the secret password for the auxiliary console ports and VTY ports on every device on the network is configured and enabled. This configuration prevents unauthorized direct access from any device on the network (Schneider, 2012).
- Ensure that all passwords are encrypted by using the service password-encryption command to prevent attackers from recovering the secret password.
- Enhance the security access to the routers and firewalls by setting a minimum character length for the passwords.
- Configure the virtual terminal lines to accept connections only with the protocols that will be needed.
- Enable the Transmission Control Protocol (TCP) to keep track of inbound connections. This approach will help protect the system against malicious attacks as well as expired sessions that are caused by system crashes.
- Disable all remote access protocols that are non-IP-based, and use SSL, SSH, or IPsec to encrypt all remote connections to the router rather than using TELNET. This approach will help ensure complete VTYs protection. Remote administration is dangerous because in case a network sniffer is on the right LAN segment; then it can access the passwords of the router and therefore be able to take control of the router (Patel, 2015).
- Disable all services and features on the router that are not needed such as UDP small services, HTTP server, CDP, IP directed broadcasts, TCP small services, boot server, IP source routing.
- Shut down all interfaces on all firewall and routers that are not used. This strategy will discourage the use of additional unauthorized interfaces. It also enforces the need for administrative permission when a new network connection is added to the router.
- Setting up all administrator’s usernames and passwords or using AAA user access Control for better audit and more control
- It is necessary only to allow local access. When the router is accessed remotely, all the telnet passwords or the community strings of SNMP are sent to the router. If in any case, an attacker collects the traffic of the network during remote access, he can capture community strings or passwords. However, if there is a need for remote access, a dedicated network management should be established. The management network must spare the interface on each router and only identified administration hosts.
Conclusion
Although the steps stated can create a secure network environment for TechLand’s network infrastructures, various other factors contribute to optimum network security. TechLand should continuously monitor for attacks as well as regularly test the state of its’ security infrastructure to ensure that the networks remain secure. A firewall alone cannot adequately deal with all the security requirements since attackers are now targeting the vulnerabilities of the network system. The company should create awareness about the importance of a secure network as well as an accountability tradition. It is also important for TechLand to acknowledge that the best network security strategies include establishing effective security policy, staying updated with the latest hacking strategies and security communities, maintaining and monitoring the whole network system with sound administration practices.
References
- Hansen, L. (1997). Network infrastructure security. Network Security,1997(6), 8-12.
- Patel, A. (2015). Network performance without compromising security. Network Security,2015(1), 9-12.
- Schneider, D. (2012). The state of network security. Network Security,2012(2), 14-20. ()
Cite This Work
To export a reference to this article please select a referencing style below:


